Device Control Software for Endpoint Protection
Device Control Software is a core element of modern endpoint security. It enables organizations to manage and restrict access to portable devices—such as USB drives, smartphones, and external storage—connected to endpoint computers. By implementing robust device control, organizations can prevent unauthorized data transfers and protect sensitive information from theft or accidental leakage.
In addition to preventing data loss, device control solutions plays a crucial role in safeguarding infrastructure integrity. By blocking unauthorized or potentially harmful devices, it reduces the risk of malware infections spreading across the network. For many industries, the use of removable media control is also a compliance requirement, making device control essential for meeting regulatory standards such as HIPAA, GDPR, or internal security frameworks.
Trusted Device Control for High-Security Industries
USB Lock RP Device Control Software is relied upon by organizations in high-security sectors such as healthcare, government, finance, defense, and energy. Designed to block unauthorized device access, enforce strict USB control policies, and ensure full compliance with regulatory standards, it delivers robust, real-time endpoint protection across the entire network.
Whether the goal is to protect classified information, maintain data privacy, or prevent malware intrusion through removable media, USB Lock RP provides a proven, centralized solution for secure USB Control in mission-critical environments.
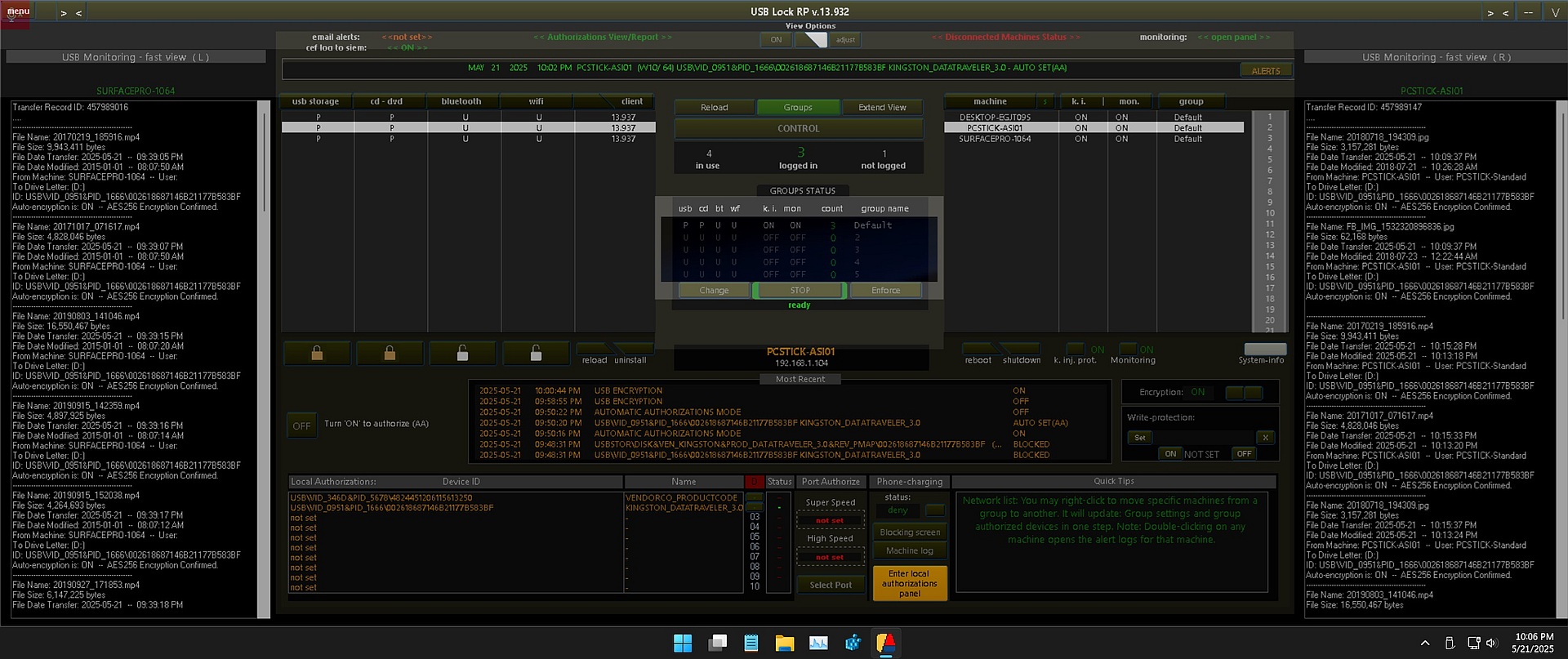
Controlling Portable Devices: Risks and Threats
Portable devices such as USB flash drives, smartphones, and external hard drives pose significant security risks in enterprise environments. These devices can be used to exfiltrate sensitive data or introduce malware into the network. Once connected to an endpoint, an untrusted device may bypass traditional defenses, compromising data integrity and opening the door to internal or external threats.
Implementing device control software allows organizations to block unauthorized devices proactively, preventing data leakage and malware infections before they occur. Without proper device control, businesses remain vulnerable to data breaches, insider threats, and operational disruptions—especially in high-compliance environments where the cost of exposure is high.

Antivirus vs. Device Control: Antivirus software is a critical part of any security stack, but it functions reactively—detecting threats only after they’ve entered the system. Device Control Software, in contrast, is proactive: it prevents potentially harmful devices from connecting at all. This not only reduces the attack surface but also conserves system resources by eliminating unnecessary scans on unauthorized hardware.
This layered security model ensures that only trusted, pre-approved devices are allowed to interact with your network—enhancing both performance and protection. Our founder, Javier Arrospide, explores this topic in depth in his recent LinkedIn article on Antivirus vs Device Control.
Endpoint Computers vs. Portable Devices
Endpoint computers include network-connected systems such as workstations, laptops, servers, and virtual machines. These devices serve as access points to critical data and infrastructure, making them key targets in any cybersecurity strategy.
Portable devices refer to removable hardware that can interface with endpoint machines. This category includes USB flash drives, smartphones, external hard drives, SD cards, and even optical media such as CDs or DVDs. While many of these devices are benign, certain forms—like BadUSB (e.g., USB Rubber Ducky)—are engineered to perform malicious actions, such as keystroke injection or stealth payload delivery, bypassing standard security defenses.
Common Devices Requiring Protection and Control
Modern device control software must manage a wide range of hardware interfaces. Devices commonly targeted for USB blocking, logging, or whitelisting include:
- USB flash drives and thumb drives
- External hard drives using USB, e-SATA, or FireWire interfaces
- Smartphones and tablets using the MTP (Media Transfer Protocol)
- CD/DVD optical drives
- Wireless communication interfaces such as Bluetooth, Wi-Fi, and IRDA
Why Device Control Is Vital for Modern Organizations
Infrastructure engineers and IT security professionals rely on Device Control Software to prevent data loss, malware infiltration, and insider threats. USB ports and other peripheral interfaces are common entry points for unauthorized hardware, making them top priorities for enforcement in endpoint protection.
As a result, terms such as USB Control, USB Lockdown, USB Blocking, and Port Control are often used interchangeably to describe this crucial security layer. The goal is to allow only trusted, pre-authorized devices while fully restricting all others, ensuring data remains secure and compliant with internal and regulatory standards.
Key Functions of Device Control Software
USB Lock RP delivers a full set of functions designed to proactively manage removable device access. Key capabilities include:
- Blocking unauthorized device connections at the USB and port level.
- Logging connection events for auditing and compliance reporting.
- Authorizing specific devices to operate only on designated machines or user accounts.
- Monitoring file transfers from authorized devices in real time.
- Encrypting files using AES-256 during USB transfer to prevent data leakage if a device is lost or stolen.
Industry Applications of Device Control Software
Organizations operating in high-security and compliance-driven environments rely on USB Lock RP Device Control Software to enforce strict usb control, reduce data loss risks, and ensure regulatory compliance. Below are key sectors where USB Lock RP supports critical operations:
- Healthcare: Safeguard electronic health records (EHR) and comply with HIPAA by blocking unauthorized USB and portable storage devices.
- Government: Protect classified systems and sensitive infrastructure with centralized USB control to secure endpoints data assets.
- Finance: Mitigate insider threats and prevent unapproved data exports in tightly regulated financial institutions.
- Defense & Military: Block threats like BadUSB and ensure secure field operations across tactical networks and classified systems.
- Energy & Oilfields: Enforce USB lockdown in geographically distributed and remote facilities to prevent tampering and data exfiltration.
- Semiconductors & R&D: Protect proprietary research and IP by authorizing only trusted devices for access and data transfer.
- Maritime & Aerospace: Control peripheral access on ships, aircraft, satellites, and command systems with precision-level device authorization.
Essential Practices and Countermeasures for Device Control
Device control tools offer a range of security measures to control usb portable devices, such as:
- Centralized USB Control.
- Whitelisting specific devices.
- USB activity monitoring.
- Data encryption.
- Event logging for auditing purposes.
Common Vulnerabilities:
Devices using protocols like USB Mass Storage (UMS), Media Transfer Protocol (MTP), or USB Attached SCSI Protocol (UASP) are particularly vulnerable to exploitation. Malicious actors can leverage these protocols to introduce malware or steal data from connected endpoints.
Countermeasures:
To address the risks posed by removable devices and unauthorized access, advanced device control software like USB Lock RP offers multiple layers of security enforcement. Key countermeasures include:
- USB Lockdown: Block all unapproved USB devices from connecting to endpoint computers.
- Driver Restriction: Allow only authorized drivers to load, preventing the use of rogue or auto-installed device drivers.
- Device Disable: Completely disable USB ports or specific device classes to eliminate unauthorized access vectors.
- Drive Dismount: Automatically unmount unauthorized external drives upon detection, preventing access or file transfers.
- Disc Ejection: Force the ejection of CD/DVD media from optical drives when not permitted.
- Screen Lock Enforcement: Activate screen locking mechanisms when unauthorized activity is detected, preventing desktop access.
Removable Media Control for Endpoint Security
Removable media such as USB drives, smartphones, and external storage devices represent a significant risk to information security when not properly controlled. Enforcing a removable media control policy ensures that only trusted devices can connect to your organization’s computers, reducing the risk of data leaks and malware intrusion.
USB-Lock-RP simplifies removable media enforcement by allowing administrators to block, approve, monitor, and encrypt USB-connected devices in real-time. Whether the goal is to secure sensitive data or meet compliance frameworks like HIPAA or NIST, our solution provides full visibility and enforcement.
- Granular device-level and port-level authorization
- Real-time alerts and logs of removable device activity
- AES-256 encryption for outbound file transfers to USB drives
- System-mode operation ensures 24/7 policy enforcement
- Integrated logging for auditing and incident forensics
For organizations seeking to control USB port access at the endpoint level with enterprise-grade precision, USB-Lock-RP offers a robust, centralized platform for managing removable media securely.
USB-Lock-RP Device Control Software
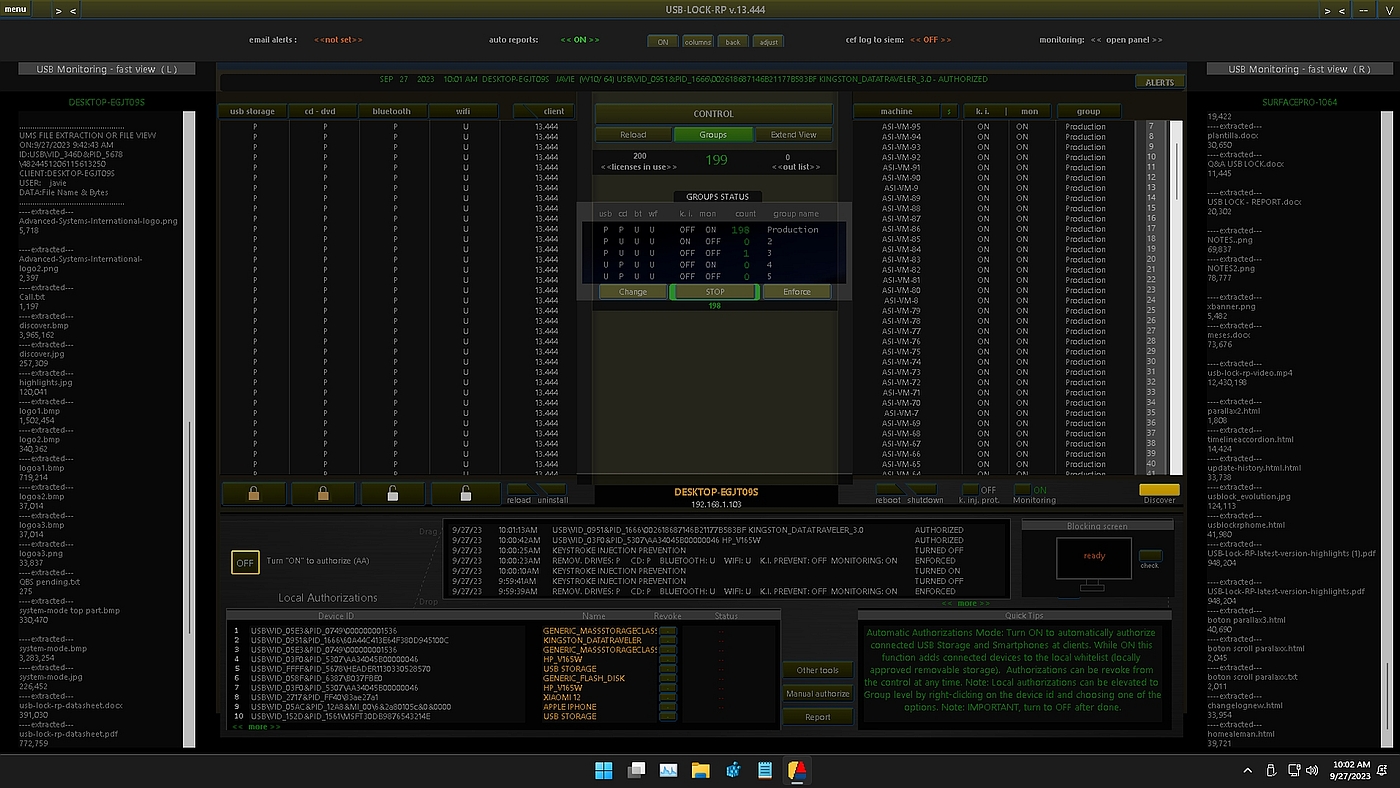
USB-Lock-RP Device Control Software is designed to block unauthorized device access, log connection events, and pre-approve specific devices to operate on designated machines when necessary. It includes monitoring capabilities to track file transfers from authorized devices and encryption features to protect data in transit, preventing unauthorized access if a device is lost. Its straightforward, centralized management interface enables organizations to streamline device access policies, monitor events in real-time, and ensure compliance with security regulations.
Why USB Lock RP Stands Out
| Feature | Benefit |
|---|---|
| Centralized USB Management | Easily enforce security policies across multiple endpoints. |
| Real-Time Monitoring | Continuously track device activity and file transfers. |
| BadUSB Protection | Block malicious devices to prevent keystroke injection attacks. |
| AES 256 Encryption | Secure sensitive data during transfers and storage. |
Efficient Multi-Admin Management with System-Mode
USB-Lock-RP simplifies secure administration with its System-Mode Configuration, allowing continuous enforcement of USB control policies even when Admin Mode is inactive. Running under the system account, it ensures secure operations during server reboots and across multiple administrator sessions.
The System-Mode interface allows administrators to define persistent enforcement rules, configure auto-activation, and streamline multi-admin workflows from a single panel.
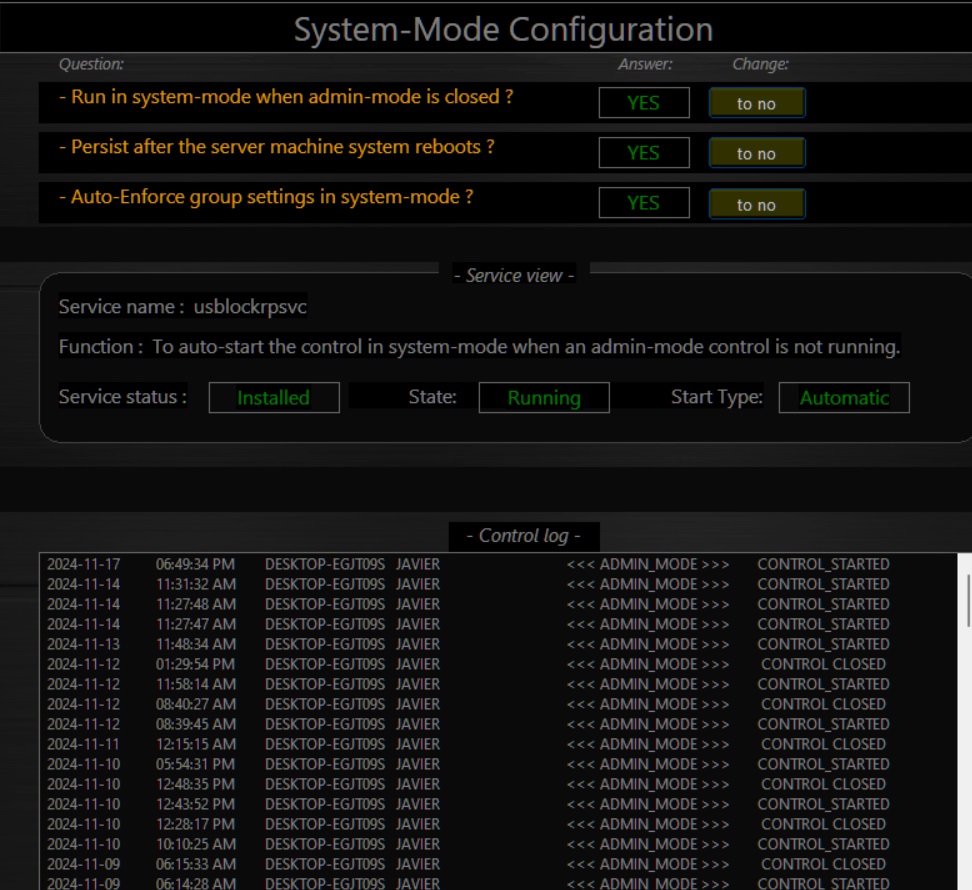
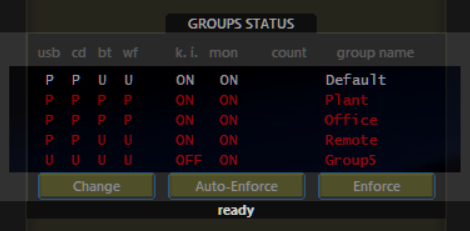
Auto-Enforce and Group Policy Management
Auto-Enforce ensures that device control policies are continuously applied across endpoint groups, even when machines log off or reboot. Administrators can apply group-level settings in real time and view overall protection status from the Groups Status Panel.
With a single click, policies can be enforced or configured to apply automatically—ensuring consistent, policy-compliant operation at all times.
Comprehensive Monitoring and Encrypted Logs
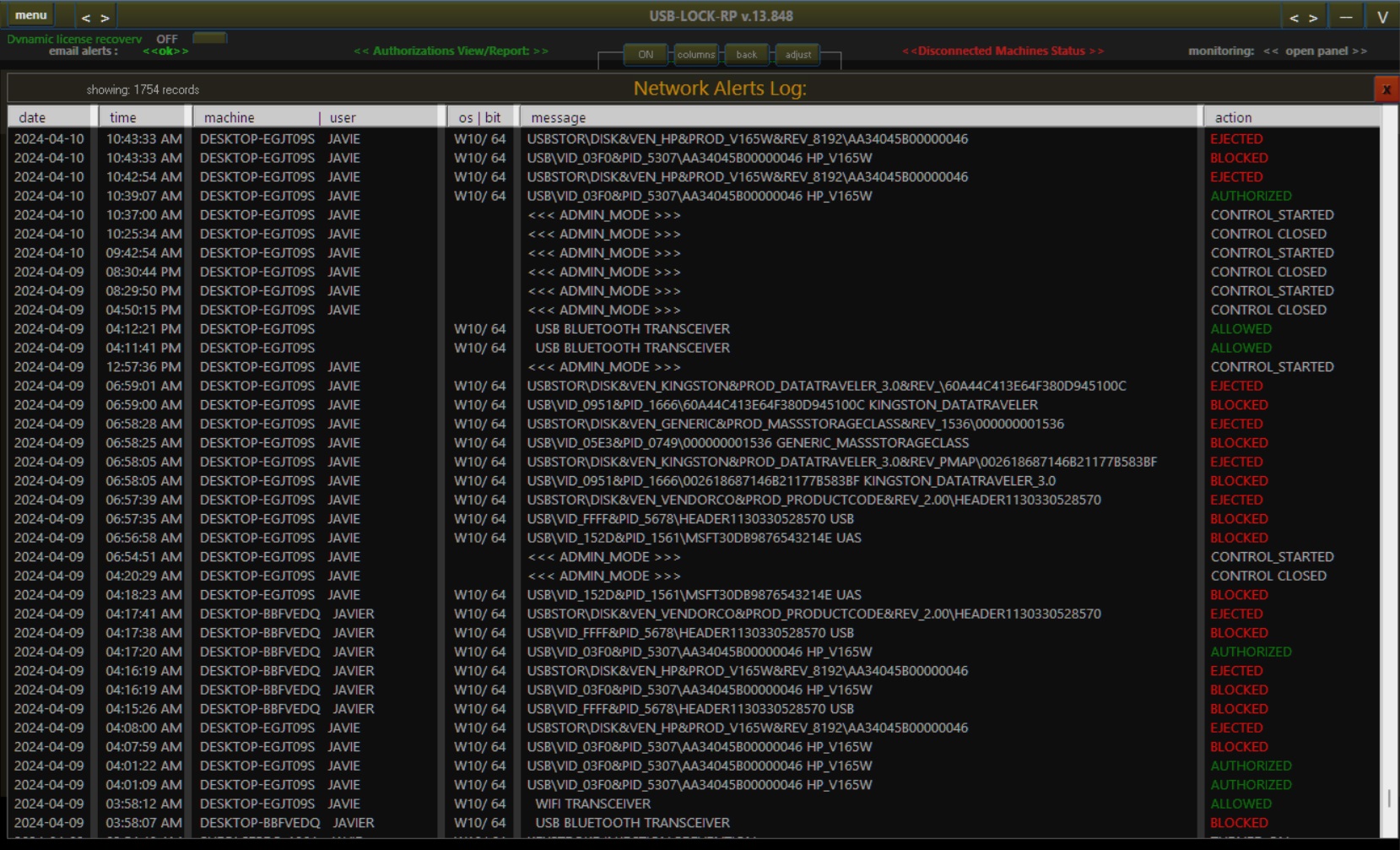
USB-Lock-RP records all USB activity in real-time logs, detailing file names, sizes, transfer timestamps, and destination devices. Logs are line-by-line encrypted using unique keys and can be exported or emailed securely on demand.
This logging infrastructure ensures full compliance and forensic-level audit capability without compromising data confidentiality.
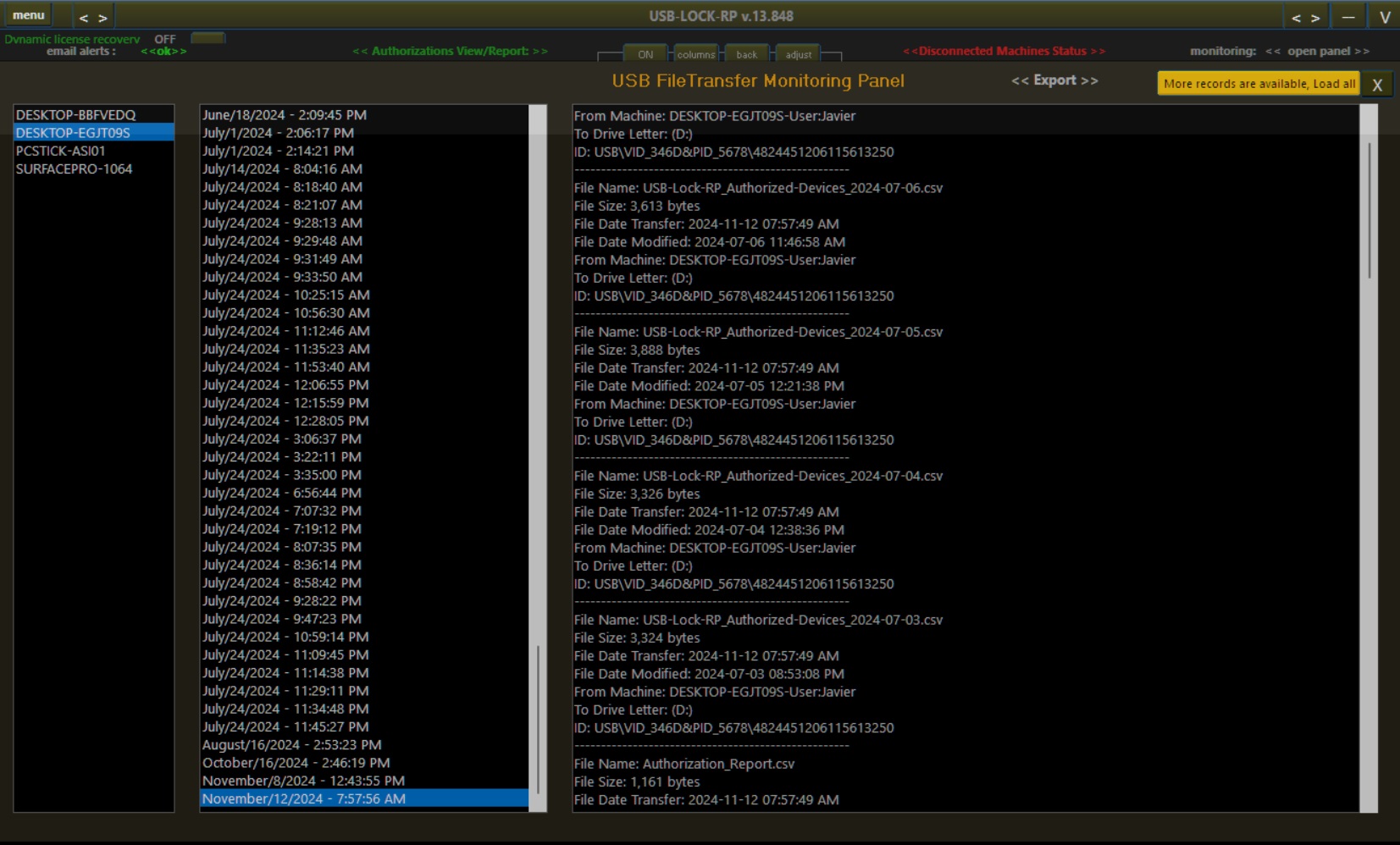
USB-Lock-RP Monitoring Logs: Providing detailed and secure logs for compliance.
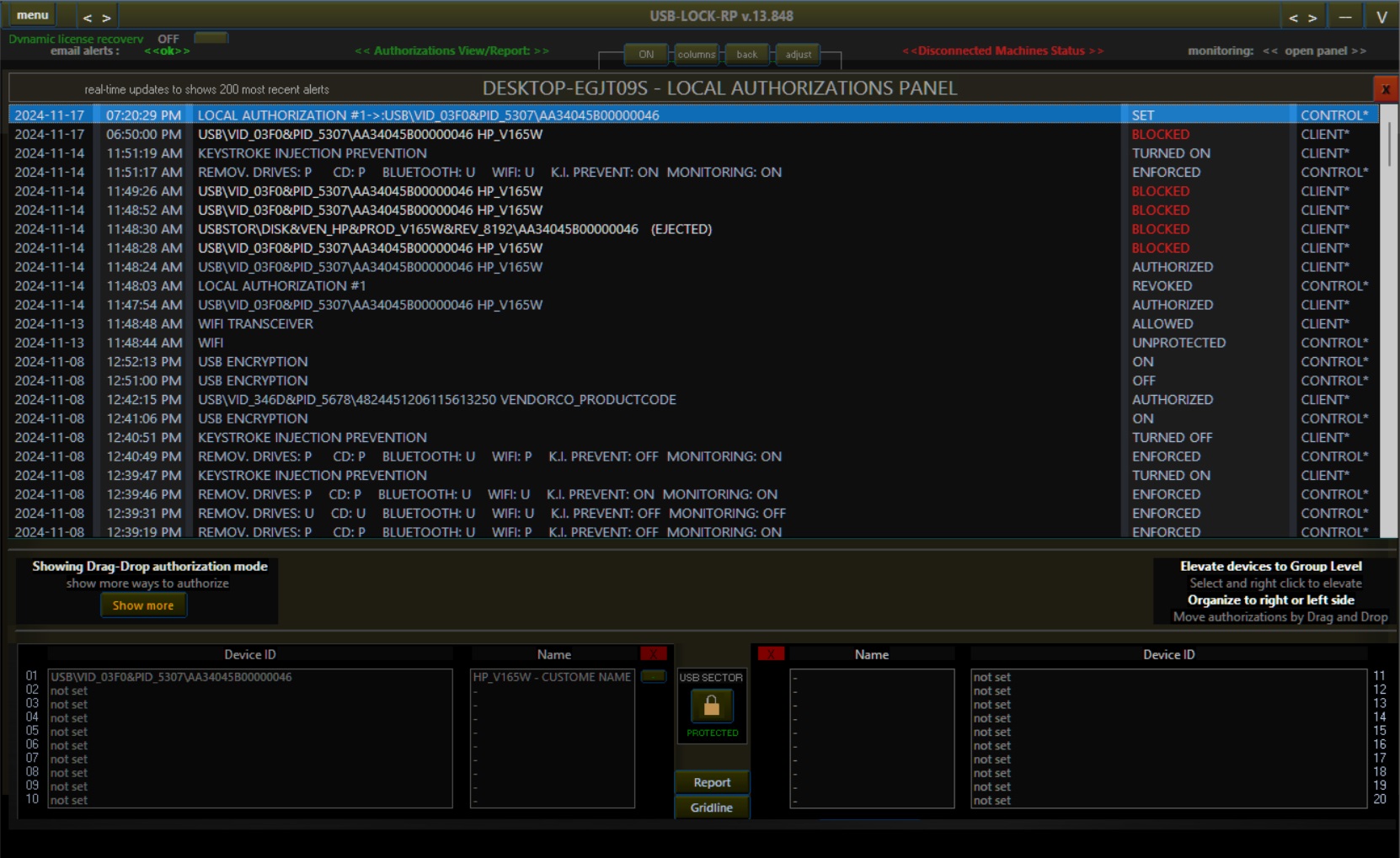
Efficient Device Authorization Management
The Authorization Panel streamlines device management with drag-and-drop approvals, real-time device tracking, and granular assignment by group or user. Devices can be quickly authorized by hardware ID, and policy changes are reflected immediately across the control network.
This simplified workflow allows IT administrators to maintain strict USB control while minimizing operational overhead.
Why Choose USB-Lock-RP?
With two decades of specialization, USB-Lock-RP has evolved from its origins in 2004 (as USB Lock AP) into a fully centralized, enterprise-grade USB Control solution. Unlike generic or cloud-reliant tools, USB-Lock-RP is engineered to operate independently—offering real-time, encrypted USB control without external dependencies. Every feature, from automated enforcement to secure device whitelisting, is purpose-built to protect endpoints and sensitive data while aligning with ethical, customer-focused development.
Trusted by organizations in regulated and security-critical sectors—including healthcare, finance, government, and defense—USB-Lock-RP has helped over 1,000 institutions worldwide safeguard data, enforce compliance, and eliminate unauthorized device access across their networks.
Why leading organizations choose USB-Lock-RP:
- Proven Expertise: Over 20 years of innovation in endpoint and USB device security.
- Scalable Architecture: Designed to support deployments from small offices to global infrastructures with ease.
- Independent Operation: Requires no internet access or cloud connectivity—ensuring full control and privacy.
- Personalized Support: Our dedicated technical team provides expert guidance for deployment, tuning, and long-term reliability.

Choose USB-Lock-RP and join the ranks of leading organizations who prioritize ethical, robust, and independently secure device control software.
Key Features of USB-Lock-RP Device Control Software
Below is an overview of the key features and benefits of USB-Lock-RP Device Control Software, delivering full control over USB devices, ports, and file transfers to help secure your endpoints, enforce compliance, and simplify administration:
| Feature | Benefit |
|---|---|
| Centralized Management | Apply and enforce security policies across all endpoints from a single unified console. |
| Comprehensive Network Overview | View real-time status and activity for every protected machine in the network at a glance. |
| Real-Time USB Control | Continuously monitor and enforce USB policies to prevent unauthorized access or data transfers. |
| Event Logging & Alerts | Log all device activity and status changes (ALLOWED, BLOCKED, AUTHORIZED) for audit and review. |
| USB File Transfer Monitoring | Track file transfers from authorized USB devices, including filenames, user, machine, timestamp, and size. |
| Color-Coded Network Alerts | Instantly assess USB status and connection history with a clear visual alert system. |
| Advanced USB Whitelisting | Authorize devices in real time using flexible approval methods and hardware ID validation. |
| Specific USB Port Control | Authorize or block individual physical USB ports, including granular speed control (USB 2.0/3.x). |
| Multilingual Interface & Alerts | Operate in English, French, or German; display localized alerts and generate reports in your preferred language. |
| Approved Devices Reporting | Generate detailed CSV reports showing all authorized devices, by user, group, or machine. |
| Full-Screen Blocking Alerts | Display immediate full-screen alerts when unauthorized devices are connected. |
| Secure Email Notifications | Receive TLS/SSL-protected alert emails for real-time security awareness and response. |
| BadUSB Attack Protection | Detect and block malicious devices designed for keystroke injection or payload execution. |
| AES-256 Encryption | Encrypt files during USB transfer to protect sensitive data, even if a device is lost or stolen. |
| Encrypted Log Storage | Encrypt server-side event logs using AES-256 to ensure log confidentiality and integrity. |
| Scalable Deployment | Efficiently manage small to large environments without performance compromise. |
| Independent Operation | Run without internet or Active Directory dependencies for full local control and air-gapped use. |
| Lightweight Resource Usage | Optimized for minimal system impact, suitable even for legacy infrastructure. |
| Perpetual Licensing Model | Includes two years of maintenance with lifetime usage rights — no forced renewals. |
| Branded Experience | Customize software visuals with your organization’s logo on alerts blocking alerts and USB control cosole. |
How USB-Lock-RP Works: Unified Control for Removable Devices
USB-Lock-RP enforces a unified security model for all removable storage devices. Upon installation, the system begins logging all USB connection events automatically. Devices are temporarily marked as “allowed” if the endpoint is in an unprotected state, but full control is easily activated through administrator settings.
Unlike traditional device control tools that require complex subtype management, USB-Lock-RP treats all removable devices—USB flash drives, external hard drives, smartphones, and SD cards—as equal risks. This approach prevents security gaps and simplifies decision-making for IT administrators.
Unapproved devices are automatically blocked and securely dismounted to prevent unauthorized access or data transfer. When exceptions are needed, administrators can authorize specific devices by hardware ID—either for individual machines or entire groups. The intuitive drag-and-drop interface makes authorization quick and traceable.
RP provides real-time, streamlined USB control with minimal administrative overhead. This unified methodology strengthens organizational security and enables IT teams to manage removable device access efficiently, even in large or distributed environments

Trusted by Top Organizations
USB-Lock-RP is the standard when it comes to protecting data assets from risk associated with the connection of USB portable storage devices in a work place.
USB-Lock-RP Device Control Software: Comprehensive Protection for Your Network
USB-Lock-RP goes beyond basic device management by offering comprehensive control over external devices. Designed to prevent unauthorized access, provides real-time monitoring and logs all connection events, ensuring complete transparency. By pre-approving specific devices, the software allows only trusted devices to operate, safeguarding sensitive data.
With centralized USB control, administrators can efficiently enforce policies across multiple endpoints, preventing data theft and malware threats. Its robust event-logging capabilities offer detailed insights into device activities, making it an essential tool for auditing and compliance. Whether your network handles removable drives, mobile devices, or wireless connections, USB-Lock-RP ensures that your organization stays secure from potential breaches.
Beyond blocking unauthorized devices, USB-Lock-RP empowers IT professionals with granular control over file transfers. Detailed tracking reports provide insights into what files are transferred, to whom, and when. Coupled with AES 256 encryption, the data remains protected during transfers, even if the device is lost or stolen. This enhanced level of security is essential for businesses aiming to comply with stringent regulations and prevent unauthorized data transfers.
"Watch the video below to see how USB-Lock-RP strengthens your network's security, blocking unauthorized devices while managing file transfers."
Scalable and Cost-Effective
Works with Windows networks of all sizes, offering flexibility and scalability to meet your organization's growing security needs. It operates independently, without requiring Active Directory or an internet connection, ensuring complete control over security policies even in isolated environments. Its minimal resource usage makes it compatible with both modern and legacy systems, enabling efficient performance without burdening hardware.
USB-Lock-RP is available with a perpetual licensing model, providing long-term cost savings. Two years of software assurance and support are included, ensuring that your organization benefits from ongoing updates and technical assistance. Personalized branding options allow the software to fit seamlessly into your professional environment.
USB-Lock-RP comes with permanent licensing, so put it to the test today! Download the official USB-Lock-RP demo (4-client capacity) and start controlling devices access to endpoint USB ports in your network.
"Our dedicated USB-Lock-RP Tech Support Team is ready to assist you with expert guidance and personalized support. We're here to ensure smooth implementation and operation of your USB-Lock-RP device control solution."
