USB Lock RP Datasheet
Advanced USB Blocking and Device Management
USB blocking and centralized management capabilities with features like smart and automatic USB device authorizations, file transfer monitoring, and flexible encryption settings, USB Lock RP empowers administrators to secure sensitive environments without compromising usability or performance.

Designed for deployment in high-security networks, airgapped environments, and compliance-focused industries, USB Lock RP offers complete control over endpoint device access. Its intuitive push-button interface eliminates the need for manual input, enabling administrators to manage devices, enforce policies, and generate detailed data insights effortlessly. Seamless integration with existing infrastructure and low resource consumption make it the trusted choice for organizations prioritizing reliability and operational efficiency.
Unparalleled USB Device Control
| Capability | Description |
|---|---|
| Real-Time USB Control | Instantly authorize or block USB devices, enforce policies, and receive alerts on connection events. |
| Centralized Management | Manage USB device access and security settings across the entire network from a single console. Generate detailed reports on security status, approved devices, and alerts, with export options in CSV format for comprehensive analysis and compliance. |
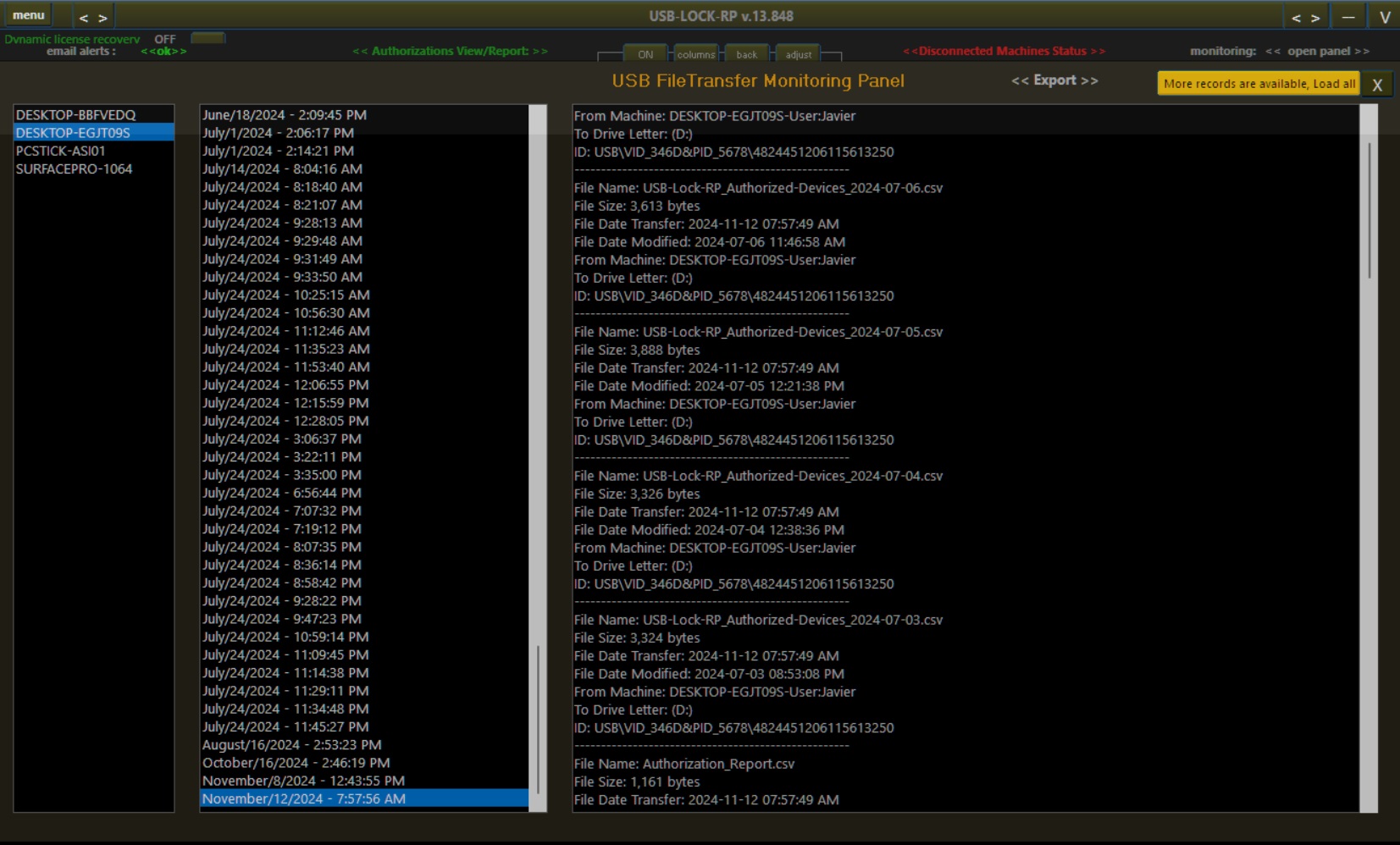
| File Transfer Monitoring | Log and report file transfers to authorized USB devices for complete data activity visibility. |
| Pre-Approve Devices | Seamlessly authorize USB devices using multiple methods, including drag-and-drop, automatic detection, or manual input, for specific machines or groups of machines, ensuring flexibility and precision. |
| USB Device Encryption | Protect data on authorized USB drives with automatic AES 256 encryption. Auto-encryption can be toggled on or off at any time, allowing flexibility for organizations using different encryption methods in their systems. |
| Granular Policy Enforcement | Apply USB control policies per group or machine for flexible and precise security management. |
| Feature | USB Lock RP | Others |
|---|---|---|
| Specialization in USB Control | Designed specifically to enforce USB security and control at the endpoint level, USB Lock RP is a centrally managed, dedicated, and mature solution for managing USB devices and ports. It addresses the real requirements of IT professionals—delivering unmatched endpoint protection and USB data security without unnecessary features or bloated functionality. | Other USB security solutions are often inefficient afterthoughts, typically offered as a basic feature in endpoint management tools or as add-ons in antivirus software, lacking the depth needed for robust USB device control. |
| Real-Time USB Blocking | Instantly blocks unauthorized USB devices, logs connection events in real-time, and applies security settings, device authorizations, or revocations without delay—delivering unparalleled real-time control for endpoint USB device security. | Delayed device authorizations and policy applications, often requiring endpoint restarts, disrupt operations and expose security gaps. |
| Connection Event Logging for USB Devices | Automatically logs all USB connection events in real-time, providing IT administrators with detailed tracking and audit trails. This ensures complete visibility over device activity, helping to enforce security policies, monitor compliance, and quickly identify unauthorized access attempts. | By contrast, other solutions often rely on limited or manual logging capabilities, resulting in incomplete audit trails and leaving organizations vulnerable to untracked USB device activity. |
| Advanced USB Device Whitelisting | Pre-approves USB devices by hardware ID with automatic enforcement, offering multiple methods to authorize devices seamlessly. USB Lock RP supports four easy ways to authorize USB devices, including drag-and-drop functionality, automatic detection and entry of hardware IDs, and manual input for precision control, ensuring unmatched flexibility and efficiency in managing device authorizations. | Basic whitelisting with limited flexibility, often relying on unencrypted ID lists stored in shared locations. This weakens security, allowing unauthorized access to authorized device information. These systems also lack streamlined authorization methods, delaying operations and increasing vulnerability. |
| USB DLP: Protecting Authorized Device Data in Transit | Encrypts data transferred to authorized USB devices with AES-256, acting as a robust Data Loss Prevention (USB DLP) measure. Ensures sensitive information remains secure while in transit. Includes real-time toggling of auto-encryption, offering seamless control as files move between devices and the network. | Most so-called USB device control solutions focus solely on protecting either the endpoint computers or the USB device data, but not both |
| Granular Policy Settings | Focuses on specific, targeted controls, allowing precise management at multiple levels, including individual devices (by VID/PID/ID), specific machines, groups of machines, or vendor/model matches. It emphasizes detailed, fine-tuned configurations to ensure comprehensive and customizable security. | Generic policies without hierarchical or device-specific controls, lacking options like vendor/model or VID/PID matching. |
| File Transfer Monitoring | Monitors and logs file transfers in real-time with detailed records, including file name, size, user, machine, and destination device, with encrypted, secure storage ensuring robust compliance. | Most often lack file transfer monitoring or provide limited, incomplete logging that fails to support comprehensive compliance or security needs. |
| Streamlined Deployment | Easily deploy clients across your organization using Group Policy Objects (GPO), other deployment tools, or pre-configured client MSI packages for rapid setup. For testing or individual installations, USB-Lock-RP also includes a client.exe setup installer, ensuring flexibility for both organizational deployment and individual testing needs. | Often rely on manual installation processes, lack MSI packages, or omit client-side components entirely. Some solutions function as passive interfaces, dependent on built-in group policies in the operating system, limiting flexibility and requiring significant manual configuration. |
| Update Control | Empowers organizations with complete control over the update process. Updates are securely delivered to the administrator via email secure download link, allowing internal distribution through USB Lock RP Control. Administrators can test updates before deployment, ensuring stability and compatibility without requiring client redeployment or external dependencies. | Relies on automatic, externally triggered updates, which can disrupt operations and bypass internal testing. This practice introduces risks of downtime, compatibility issues, and potential vulnerabilities, especially in critical infrastructure environments. |
| Autonomous Control | Ensures full functionality without reliance on internet connectivity or cloud services, supporting air-gapped and high-security environments. | Dependent on external servers or cloud, increasing exposure to operational disruptions and security vulnerabilities |
| Discovery Function |
Provides comprehensive, real-time insights into system and connected device information, including:
|
Lacks HID-focused auditing or comprehensive system reporting. Minimal to no real-time device information and limited value for OT/ICS/SCADA networks. |
Requirements
- Network TCP/IP
- Windows Operating Systems:
- Modern Systems: Windows Server 2022, Windows 11, Windows Server 2019, Windows 10, Windows Server 2016, Windows 8.1.
- Legacy Systems: Windows Server 2012 R2, Windows 8, Windows Server 2012, Windows 7, Windows Server 2008 R2, Windows Vista, Windows XP, and Embedded POSReady 2009.
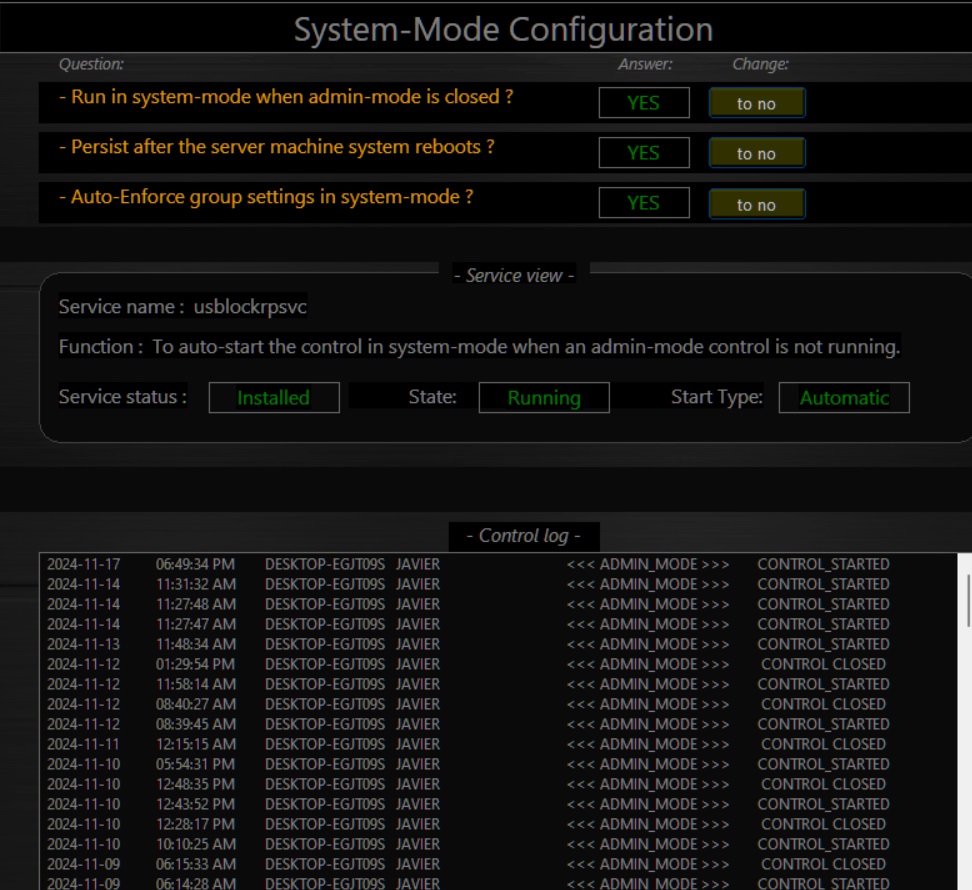
Automatic Authorization Mode: The Friendly Approach
USB Lock RP’s Automatic Authorization Mode (AA), often referred to as the "friendly mode," simplifies the initial implementation process by approving devices as they are connected during its activation period. This ensures only devices actively needed by informed users in the designated group are authorized, eliminating the guesswork associated with outdated or irrelevant "whitelists". Unlike traditional discovery features in other solutions, which merely list previously connected devices, AA actively builds an up-to-date authorized device list based on real-world usage.
USB Lock RP improves USB device control by enabling secure operations through automated and real-time device authorization. Administrators can activate AA for a specific group of machines where users connect devices they regularly require. During this phase, connected devices are automatically added to the local authorized ID list at the control. This eliminates the need for manually typing IDs or importing outdated lists, ensuring that only relevant devices are approved for use.
After a brief onboarding period, AA is deactivated, and security policies are enforced. Unauthorized removable drives or smartphones are immediately blocked, while authorized (whitelisted) devices remain fully operational. This dynamic process allows organizations to replace old whitelists and adopt a modern, automated approach to device authorization.
USB Lock RP’s AA Mode not only saves time and reduces administrative effort but also ensures policy compliance by accurately reflecting the devices required for real-world operations. IT professionals can further refine permissions in real-time, revoke or elevate authorizations as needed, and confidently enforce security without gaps or oversights.
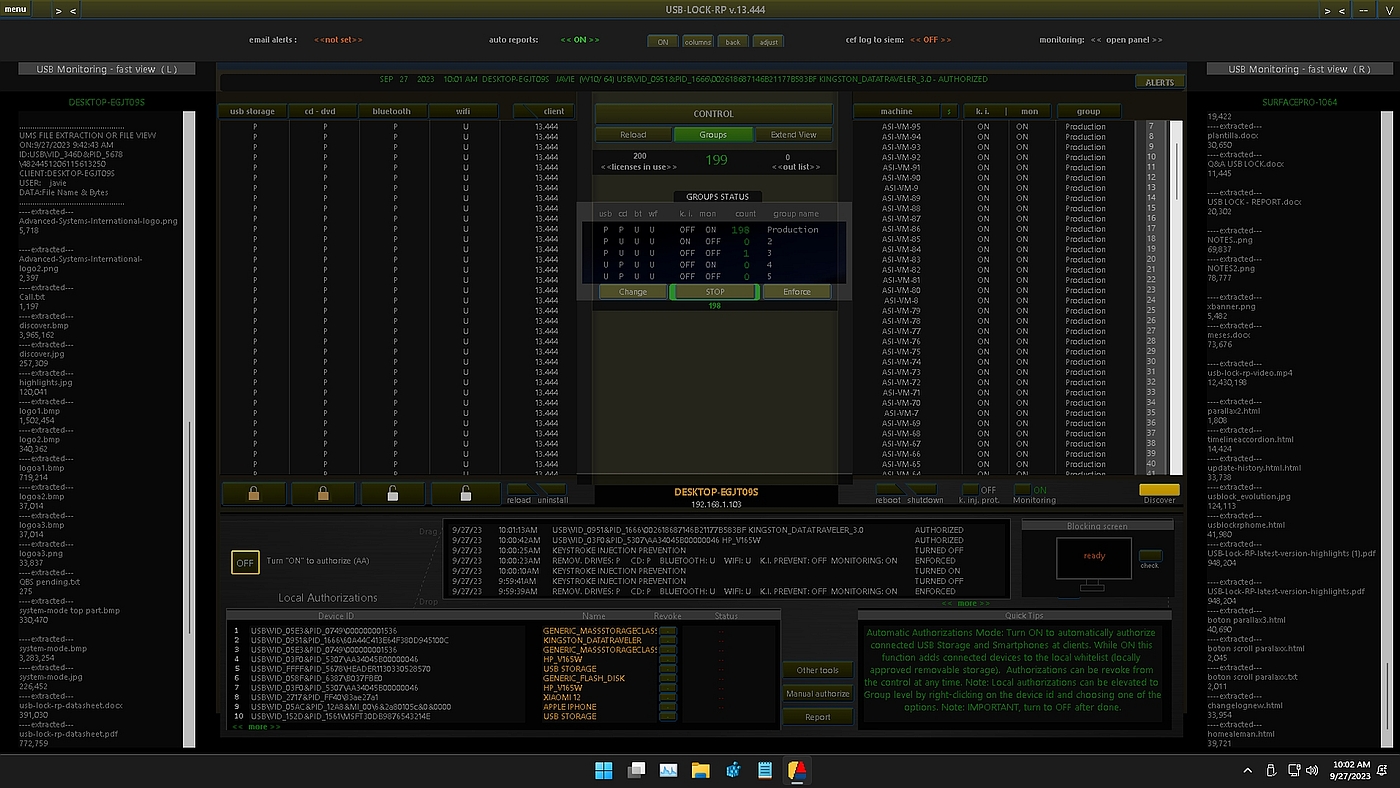
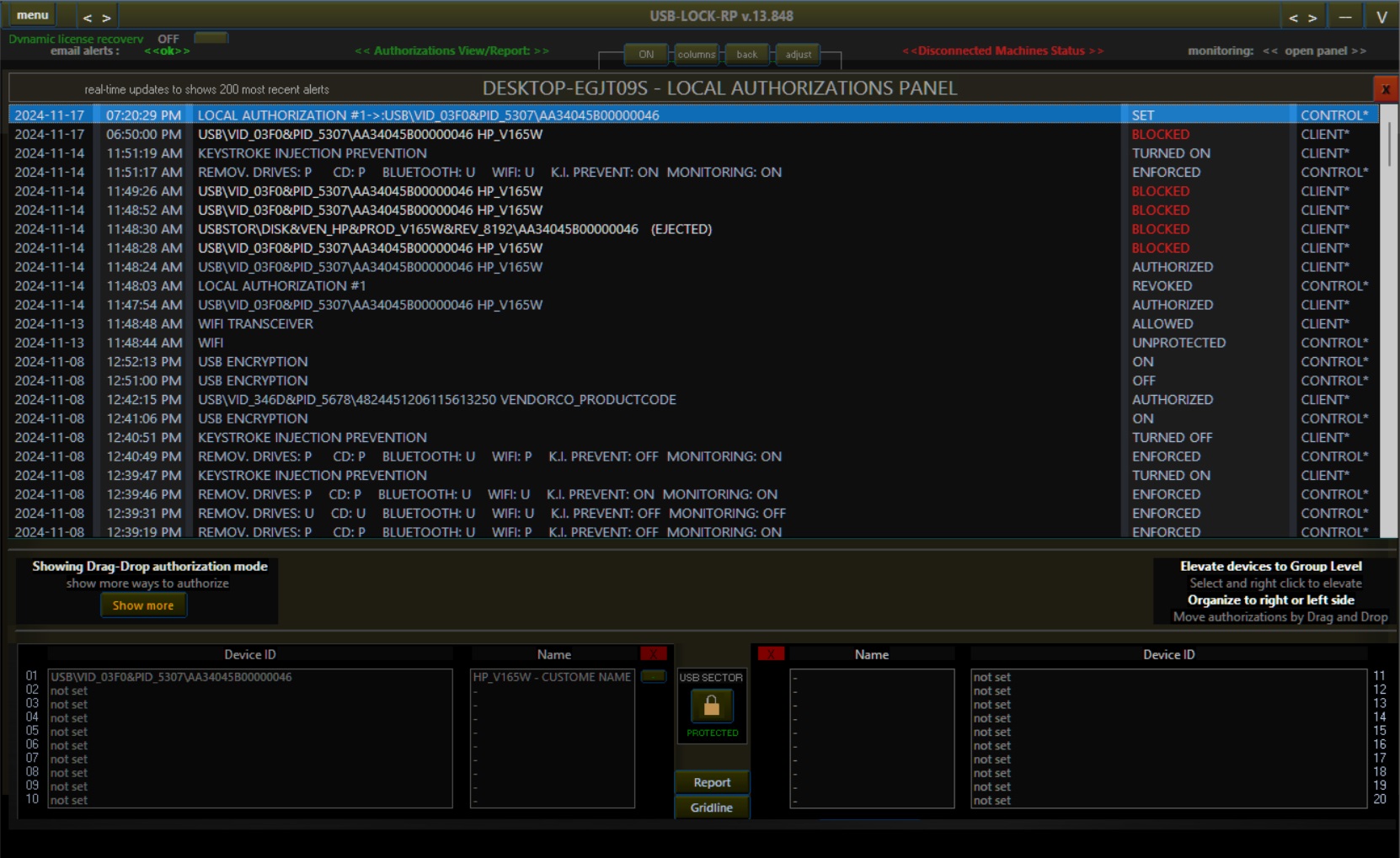
USB-Lock-RP Device Control Software (Main screenshot).
Unified Security for Removable Devices
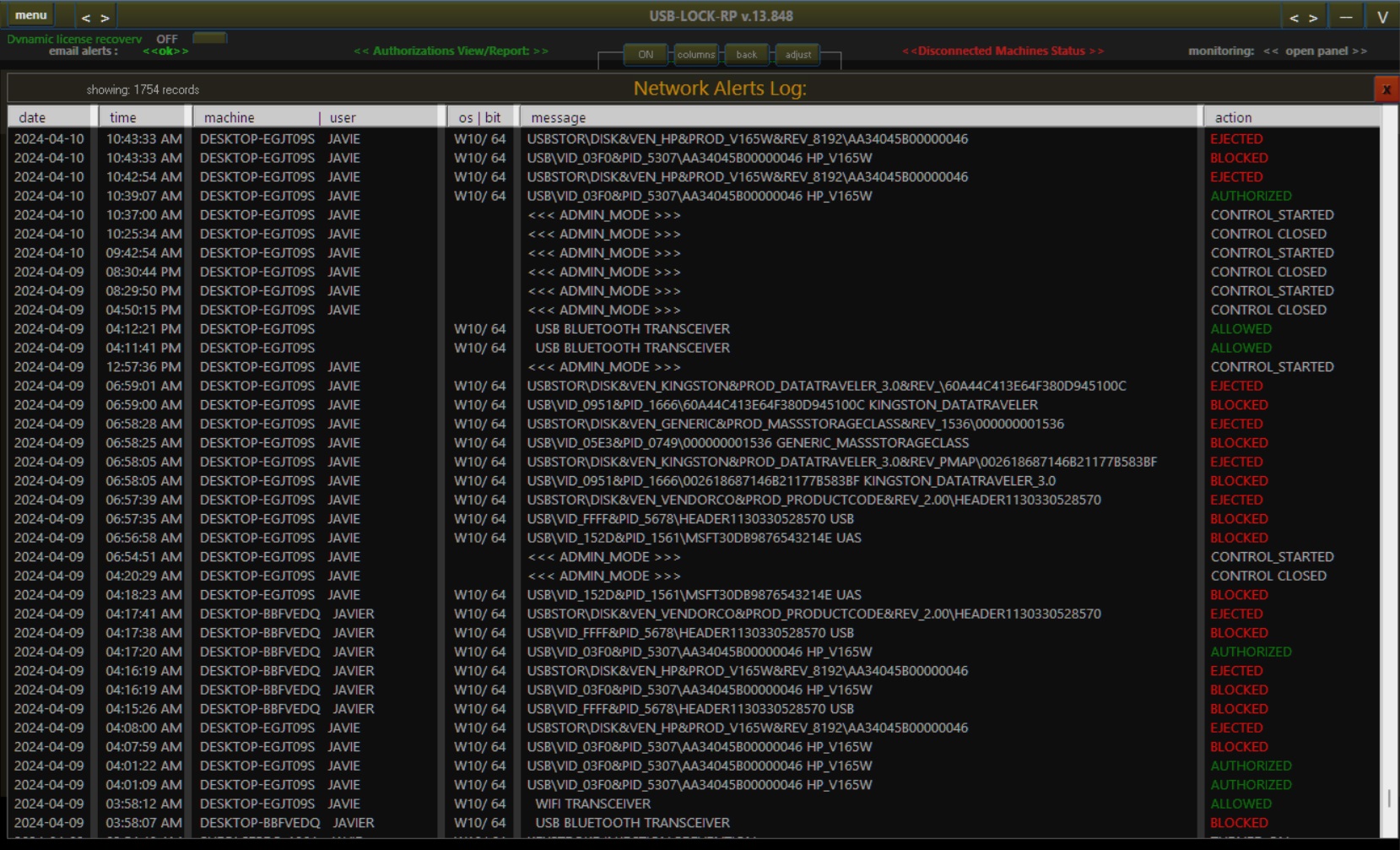
By default, upon installation, USB Lock RP automatically logs all USB device connection events, marking devices as "allowed" if the system is in an unprotected state. Blocking removable drives or other device types, however, is a straightforward, administrator-led action.
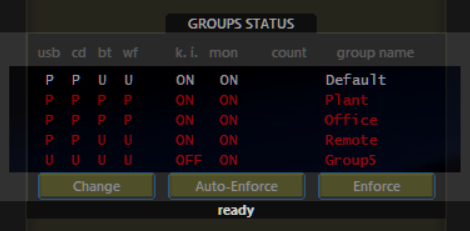
Unlike traditional solutions with complex subtype management, USB Lock RP adopts a unified security model. It treats all removable storage devices—such as USB flash drives, external HDDs, smartphones, and SD cards—as equal security risks. This approach streamlines decision-making for administrators, ensures policy compliance, and eliminates gaps that might arise from overlooked device categories.
Unapproved storage-capable devices are blocked and correctly dismounted to prevent unauthorized access. Devices required for operations can be easily authorized by hardware ID, either for specific machines or entire groups, ensuring flexibility without compromising security. Alerts for connection events streamline the authorization process, allowing administrators to use a drag-and-drop interface to quickly approve devices and elevate them to groups as needed.
This approach eliminates the need for traditional whitelists, reducing administrative overhead while providing robust, real-time protection. USB Lock RP’s philosophy ensures that organizational data remains secure, while its intuitive design enables efficient management for IT professionals.
Core Features of USB Lock RP
- Real-Time USB Blocking: Instantly authorize or deny USB devices based on granular rules.
- Centralized Management: Control USB device access and enforce policies across the network from a single console.
- File Transfer Monitoring: Log and track file activity to ensure compliance and security.
- Granular Device Authorization: Whitelist devices by hardware ID, vendor, or model for precise control.
- Endpoint Protection: Safeguard air-gapped environments with built-in functionality, eliminating reliance on external servers.
Real-World Use Cases and Advanced Capabilities
Critical Infrastructure Protection
- Deployed in air-gapped and high-security environments to prevent unauthorized USB device connections.
- Safeguards ICS systems and OT networks by implementing robust security measures and detailed HID reporting, providing visibility into open interface and endpoint pipe communication requests and data exchanges.
Compliance and Audit Readiness
- Delivers endpoint protection tailored to high-security environments, ensuring compliance and robust defense against unauthorized devices.
- Meets regulatory requirements (GDPR, CMMC, ISO 27001) through real-time monitoring and logging.
- Provides comprehensive data encryption to ensure sensitive information remains secure.
Future-Ready Security
- HID Discovery anticipates emerging threats and is designed to enable defining security rules based on device characteristics in future updates.
- This ensures secure endpoint control by enabling real-time USB device authorization and advanced blocking capabilities.
- Mitigates risks of advanced HID-based attacks, such as keystroke injection and rogue devices.
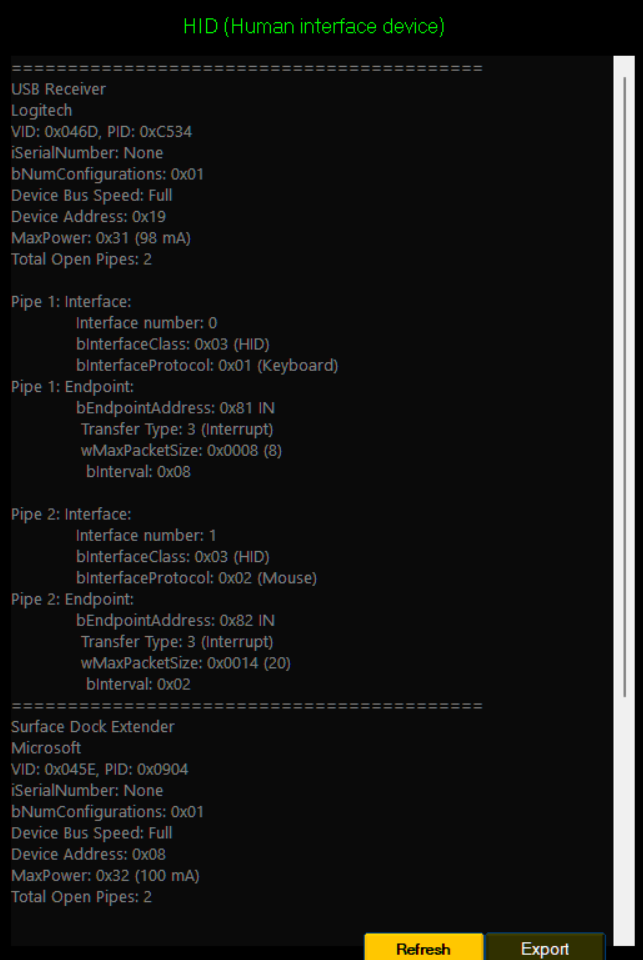
Example of a low-level HID report showcasing device details, power consumption, and endpoint configurations.
USB-Lock-RP leads the industry in proactive and detailed device control capabilities, preparing organizations for current and future security challenges.