Removable Media Policy Enforcement
In the context of Information Governance and Security, Removable Media Policy enforcement refers to measures, controls and tools managed by IT infrastructure and/or security administrators to ensure that removable media policy guidelines are followed and enforced.
Removable media policy acknowledges that the unapproved use of storage capable portable devices or media, present risk to data assets and rules that such devices or media should not be permitted to be used in the organization computer infrastructure.
USB ports dominate as the primary medium for physical data transfer in modern computers, which is why managing removable media is often referred to as USB Device Control.
Removable Media and Devices: Many types of storage media and devices that can be inserted into and removed from computers are available. In modern computers most connect via a USB port and communicate through a device protocol interface. The most used protocols are USB mass storage (UMS), USB Attached SCSI (UASP) and Media Transfer Protocol (MTP).
examples:
- Removable drives: (USB MSC): Flash drives, thumb drives, memory sticks, flash memory cards etc
- Portable Storage: (USB-MTP): smartphones (android, iPhone), tablets, cameras etc.
- External drives: (USB UAS/MSC, e-Sata, Firewire): HDD/SSD drive/enclosures etc.
- Optical discs: (USB MSC): CD-ROM, CD-R, CD-RW, DVD-ROM, DVD-R, DVD RW, Blu-ray etc.
It’s relevant to note, that Composite devices are designed to communicate through multiple interfaces and may contain more than one data storage medium.
Removable media refers to:
- A data storage medium that can be inserted (e.g., a Compact disc) into a media reader/writer:
- internally attached to a computer(e.g., a smartcard inserted into an internal card reader)
- external to a computer. (e.g., a CD inserted to an external CD-ROM that connects to a USB port)
- An integrated data storage component of a portable device (e.g., USB flash drive, that connects to a USB port)
Enhancing Removable Media Control
Implementing a comprehensive Removable Media Policy is crucial for maintaining a secure organizational environment. This policy can be enforced using Group Policy Object templates or through the utilization of specialized USB device control software tools, offering a more robust and actively controlled solution with real-time response.
Now, let's delve into the advantages of leveraging a dedicated security control tool for effective Removable Media Control. Meet USB-Lock-RP Device Control, a cutting-edge security software tool designed to provide centralized control over removable media access to computers. This powerful tool offers a range of capabilities, including the ability to block, approve, monitor, and encrypt USB devices, all applied without delay.
USB Lock RP a straightforward Removable Media Policy Enforcement Tool, that helps control removable media and devices like no other software does.
Management advantages:
- Real-time response, set/change/enforce without delay. (Granular and Groups management). This is important as delays in policy approval/disapproval enforcement can negatively affect security.
- Straightforward, presents a birds-eye view of endpoints security status on the main interface, allows going from micro to macro management effortless in no time. This clarity has an important positive impact in security.
- Automatically receive, show and log devices connection events, this greatly enhances security value and from an audit/forensic perspective this is a must.
- Keeps logs secured, it’s considered important that even at the administrative server level logs containing devices IDs and other working data are secured. Working data is only readable within the USB Device Control interface or when reports are created. (On demand or automatically if set)
- 24x7 surveillance and enforcement. The administrative control can be set to run in System-mode and continue to receive connection alerts and enforce settings around the clock even if no administrator is logged.
- Capable of Monitoring and auto-encrypting approved devices file transfers from endpoint to device, (Only available for USB Removable drives) this offers an option to transfer files from an endpoint to another, protecting data in transit, so if a device is lost or stolen data remains secure.
Advantages at endpoint, client-side:
- Full screen blocking client-side shows organization Logo (always) and optionally a custom paragraph to inform employee on how to request device approval.
- Light on endpoint system resources. USB-Lock-RP clients average 0% CPU consumption.
- Capable of restricting Wi-Fi adapters, USB Bluetooth file transfers and includes an automatic function to prevent on-the-go keystroke injection attacks, the function offers an alternative to having to approve each keyboard and docking stations in the network as this can become unrealistic depending on the network size.
- Security strength: The image below shows a bit on how the tool manages removable media from and endpoint perspective and could be used a guide as to what to test and expect on your environment.
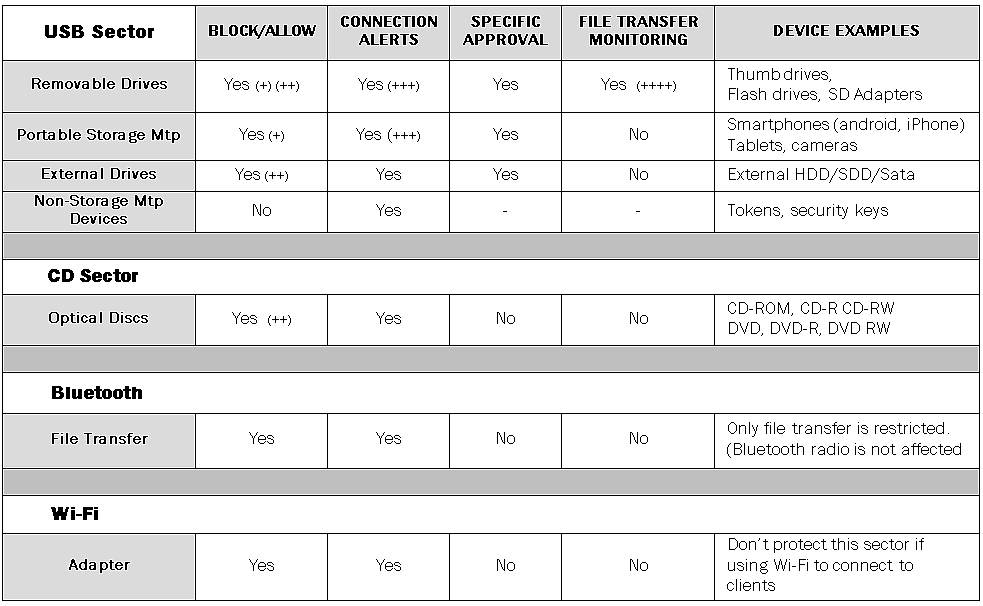
(+) Lockdown, Full screen blocking client-side. (Shows Logo and optionally a custom paragraph.)
(++) Dismount, Ejection.
(+++) Alerts include Friendly name (As well as Hardware Identifiers, Event date and Outcome.
(++++) Other Capabilities included: File transfer Auto-Encryption & Specific USB Write protection.
At a glance:
The administrative console can be installed on any Windows Server/station in the network and allows to control devices access from a central location. Its straightforward control interface is easy to operate and settings are enforced to clients in real-time.
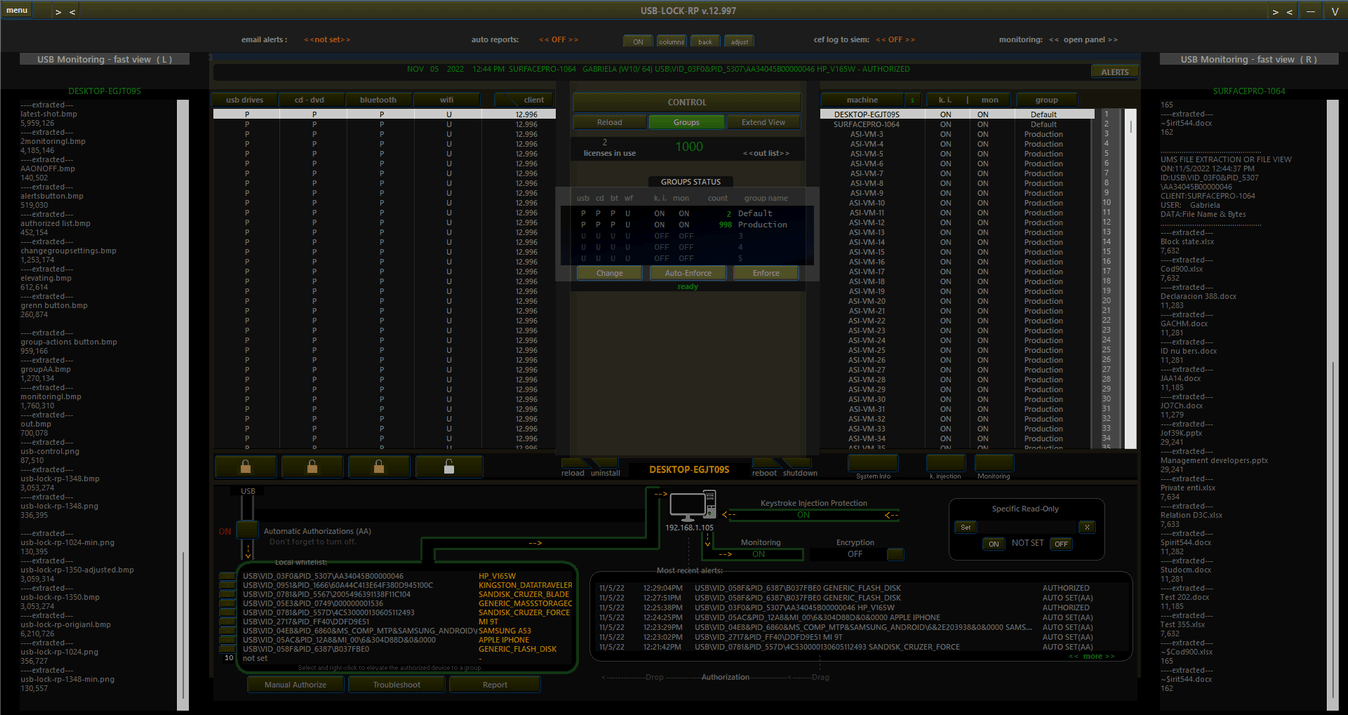
Allowing only authorized usb devices:
Removable media control policy requires that only approved portable devices can be used. This approval process might require paperwork and instances external to the software scope. Nevertheless, security administrators can use the tool to make effective such approvals in the network and authorize devices as required.
The tool can authorize approved removable drives and portable storage in such a way that only authorized usb devices are allowed. This way subsequent connections of pre-approved devices are permitted and the device can function normally.
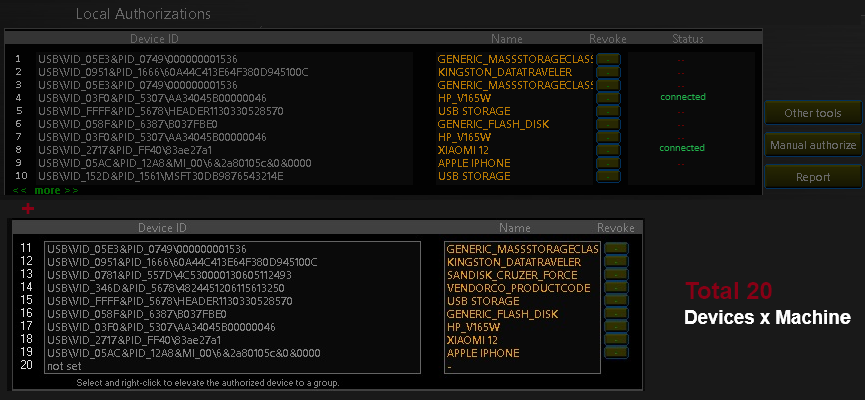
USB authorize function characteristic:
- Authorize by specific device ID match.
- Authorize by device Vendor/Model ID match (VID-PID match).
- Authorize devices on specific computers or groups of computers.
- Acquire device IDs and approve devices automatically upon connection.
- Approve by entering device ID manually.
- Approve and authorize device by drag and drop from the most recent alerts panel.
- Delete or Reject authorizations at any time without delay.
- Ideal to protect ICS Industrial control systems and corporate offices.
- Report authorized devices on specify machines or groups on demand.
Approving USB devices automatically:
Automatic authorization refers to the software capability to acquire the device ID and friendly name automatically to approve USB devices upon connection. This way subsequent connections of the USB device are allowed. Automatic authorization mode can be turned ON or OFF with one click at local level or be deployed to groups with ease.
Other Capabilities:
- Approved devices file transfer monitoring.
- Auto-Encryption to allow securing data in transit.
- Specific USB Write protection
- Auto-enforce function to watch over group settings and make sure they are kept at client endpoint.
- System-mode to allow the console to continue to run, receive alerts and enforce security silently while the admin. console is not running. This function allows 24x7 survailance and proper removable media control.
Our demo will give you a complete understanding of USB Lock RP and how device control can help you implement and Enforce Removable Media Policy in no time. If you have any questions, our support team is always ready to assist.
Download usb lock demo version
(5 client capacity).
or
Request courtesy licenses for a complete Proof of concept review.
(Licensed and personalized, 10 client capacity).
